
One of my favorite sessions I attended at WWDC this year was entitled "Your Apps and Evolving Network Security Standards." I highly encourage anyone to watch the video who has not already. It was a session covering all of the latest network security enhancements that Apple is supporting across their platforms. One of the key takeaway's from this session is all of the work Apple is doing with ATS (Application Transport Security), in particular, the support for the latest TLS specification, TLS 1.3. It was during this session that I first heard about the latest TLS specification and was very intrigued because of all of the security and speed enhancements TLS 1.3 gave over previous versions of TLS. And that is why I wanted to write this post, to give a brief overview of what is better, faster, and stronger about the latest version of TLS, and to provide a real world example on how adopting this new specification could enhance your application's performance. And lastly, provide links on where to find all the latest information on the TLS specification as it is being drafted, revised, and reviewed.
Introduction: What is TLS?
So, before we begin on TLS 1.3, I thought it would be handy to give a brief overview of what TLS is and why it is so important in the world of network security. TLS stands for Transport Layer Security and it is the preferred security protocol used to establish secure network communication between two applications.
To begin, let's take a look at standard HTTP communication as an example. First, standard HTTP communication consists of a client and server acknowledging one another to open a socket connection. Next, data is transferred between the two applications. And lastly, the connection is closed. All of these steps listed transfer data in plain text communication. TLS on the other hand, is a protocol used to provide a layer of security in that communication. TLS provides a standard in which a secure connection can be established, a key exchange can be negotiated, and then encrypted data can start being passed back and forth between the applications. None of which is done in plain text. This is why TLS is so important, it provides a secure way to transfer information between two applications.
A typical TLS packet exchange to open a socket connection between a client and a server would look something like this:
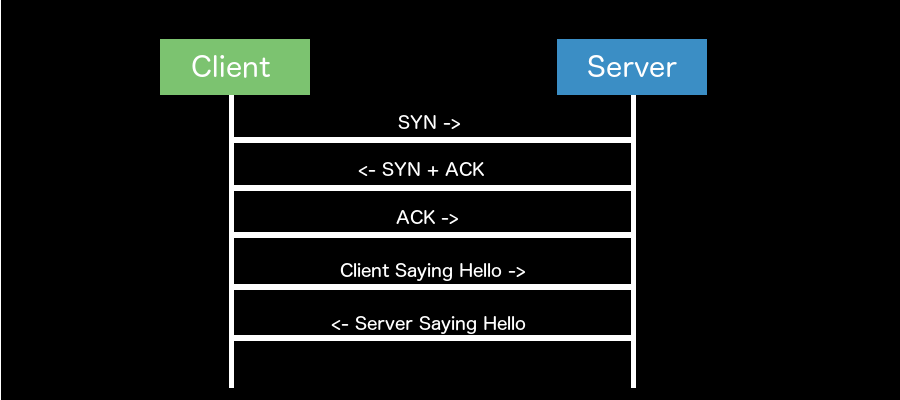
In the diagram above the TCP packet exchange depicts how a client and a server exchange synchronized and acknowledgement packets in an attempt to perform the TLS handshake. The TLS handshake is used to open a secure socket connection/session between applications. The TLS handshake depicted above then sets up the key exchange so that the client and server can successfully negotiate a cipher suite and encrypted data can start being transferred back and forth.
A depiction of how this TCP packet exchange works is provided below:
TLS 1.3: Better
So, what makes TLS 1.3 better as opposed to previous in-use versions of TLS? Well in my opinion, at least two different features make 1.3 better than the previous; First, forward secrecy has been improved and all static RSA and Diffie-Hellman cipher suites have been removed. So what does that mean and why does that make TLS 1.3 better? Forward secrecy is the protection that ensures that even if keys are compromised, past sessions that use those keys cannot be compromised and data from those sessions cannot be decrypted. Thus providing forward secrecy for past sessions and improving the security over previous versions of TLS.
Second, the list of symmetric encryption algorithms supported has been shortened in TLS 1.3. At face-value, this probably does not sound like a feature that makes TLS 1.3 better, but let's take a deeper look at what does this means and how and how this feature improves the security of TLS 1.3 compared to previous versions. First, what is symmetric encryption? Symmetric encryption is the usage of one key for both encryption and decryption of the cipher between both parties involved in the communication. Second, how does reducing symmetric encryption support make TLS 1.3 better than previous versions? Symmetric encryption has been a technique used for a long time now now and works very well for certain use-cases, but in my opinion, introduces risk due to all parties involved needing to exchange the key to decrypt information. Reducing the amount of symmetric encryption algorithms supported in TLS 1.3, is in my opinion, a reduction in risk in favor of asymmetric encryption algorithms.
TLS 1.3: Faster
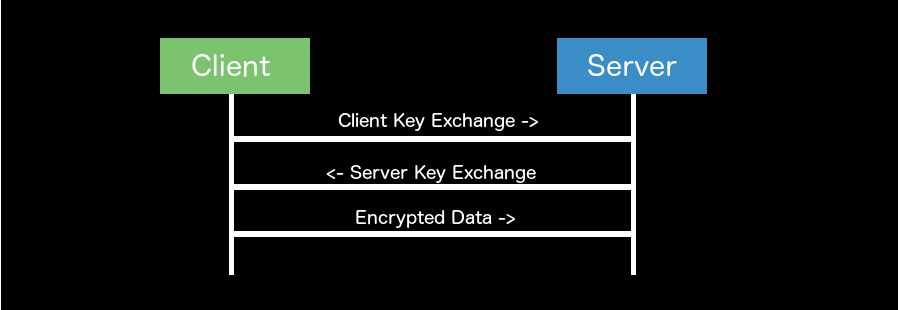
Next, let's discuss what makes TLS 1.3 faster than previous versions. One of the biggest speed enhancements that sticks out in my mind, and quite honestly why I am so excited about TLS 1.3, is the speed enhancement referred to as 0-RTT. So, what is 0-RTT and how can this new feature improve the speed of my application? Well, first, 0-RTT stands for zero round trip time and saves a full round trip while setting up the secure connection and negotiating the key exchange. If you look back at the two diagrams I posted above you will notice, that in an asymmetric situation, a round trip is made for both applications to say hello to each other, and then, to negotiate the key exchange. In TLS 1.3, 0-RTT is a technique developed to negotiate the key exchange while both applications are saying hello to each other. Consolidating two round trips into one and thus saving a full round trip and potentially lowering the latency of setup time compared to previous versions of TLS.
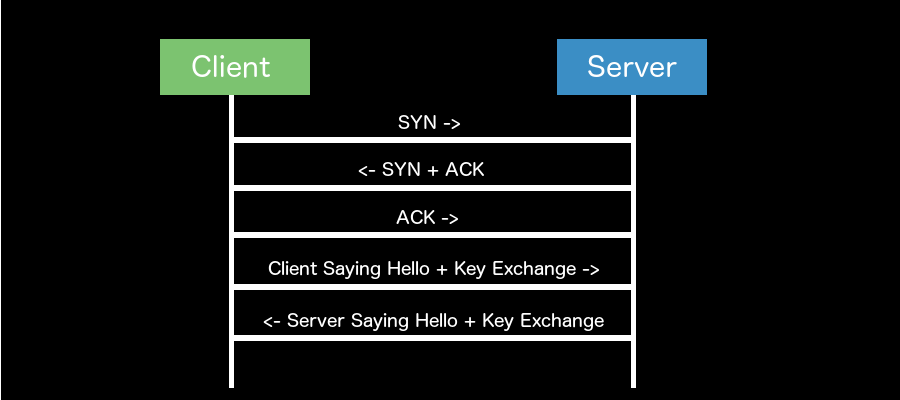
Above you will see a consolidated diagram that depicts how the packet sequence will flow in in TLS 1.3 while the connection is being established. As mentioned above, one of the key differences you will probably notice is the consolidation of steps for saying hello and the negotiation of keys illustrating the connection time saved using 0-RTT.
Looking at the diagram above, the time savings for 0-RTT may not seem like much, but in the world of iOS, watchOS, or other embedded devices where connections are often made over cellular networks, this can be a pretty large win. I can remember sitting at WWDC in the network security session and hearing Apple announce that TLS 1.3 connections could see speed enhancements of up to 30% due to 0-RTT. This is huge and would be a noticeable speed enhancement for almost all applications!
TLS 1.3: Stronger
Now let's discuss what make's TLS 1.3 stronger than previous versions. One of the first things that comes to mind is the improved security of data that used to be previously sent in plain text. For example, the TLS specification states that all messages sent after the Sever Hello packet will now be encrypted, thus protecting handshake packets while the connection is being finalized.
Next, TLS 1.3 now supports the use of Elliptic curve algorithms as a way to perform public key exchange. Elliptic curve algorithms provide a key that is smaller in size but just as secure as most RSA keys. Thus providing a security boost and performance boost all at the same time. So, what is an Elliptic curve algorithm and how do they work? Unfortunately, a detailed answer to this question is outside the scope of this blog post, but generally speaking, Elliptic curves are a way to describe a public key using a mathematical equation that can be represented on an algebraic plane. Thus replacing large RSA public keys that come in numeric form and reducing the overall transmission size of the key exchange.
In Summary ⌛️
# To enable TLS 1.3 on macOS High Sierra $ sudo defaults write /Library/Preferences/com.apple.networkd tcp_connect_enable_tls13 1
In summary, many exciting things are on the horizon with the new specification of TLS 1.3. One real world example that I am very excited for is to see what this this new protocol will do for all iOS and watchOS applications that make many secure network connections. I am looking forward to realizing that 30% speed increase Apple spoke of at WWDC. Even if your application is only making 10 secure network connections that take 2 seconds for each connection, this is still a large win and as an application developer you could still realize a large gain in speed for from TLS 1.3!
I am very excited to get in and start taking advantage of what's better, faster, and stronger with TLS 1.3. Apple is letting users developing on macOS High Sierra take advantage of this feature today by running the command above in your terminal to enable the draft version of TLS 1.3. As of today, installing the mobile provisioning profile on an Apple Watch or an iOS device will not work due to the expiration of mobile profile. Hopefully by this year's WWDC TLS 1.3 will be out of draft and ready to use on a mobile device!
To learn more about the TLS 1.3 specification, you can review the draft specification being created on Github here: https://github.com/tlswg/tls13-spec. Please let me know if you have any questions, comments or concerns on any of the topics I discussed in this article. And as always, thank you for reading! 😀
References:
- TLS 1.3 Specification on Github: https://github.com/tlswg/tls13-spec
- IETF TLS Working Group Documents: https://datatracker.ietf.org/wg/tls/documents/
- App Transport Security: https://developer.apple.com/library/content/releasenotes/General/WhatsNewIniOS/Articles/iOS9.html
- Forward Secrecy: https://www.sans.org/reading-room/whitepapers/bestprac/correctly-implementing-secrecy-35842
- Symmetric Cryptography: https://www.ibm.com/support/knowledgecenter/en/SSB23S_1.1.0.14/gtps7/s7symm.html
- RSA Encryption: http://mathworld.wolfram.com/RSAEncryption.html
- Diffie-Hellman Key Exchange: http://www.math.ucla.edu/~baker/40.1.99w/handouts/rev_DH/node1.html
- Elliptic Curve Cryptography: http://ieeexplore.ieee.org/document/814351/



